I recently wrote a blog called What should I log in my SIEM? and someone recommended that I do a follow up on what Windows Event logs are helpful in addition to the Security log. It’s a truth universally acknowledged, that a SIEM must contain Windows event logs. But which ones?
I think this will end up being several posts because there is a lot to cover here but I thought I would start with which logs you need to populate my favorite workbook.
In Sentinel, Workbooks are dashboards. You use Workbooks to view insights gathered from data collected from various sources. They're kind of like a canvas that you can use to paint the data you want to see at a glance.
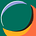
One of my favorite Workbooks is called Insecure Protocols. When you ingest the required data, it can report on use of unsigned LDAP traffic (which is susceptible to replay or attacker-in-the-middle attacks) or use of SMBv1 (which continues to be a primary component in destructive ransomware attacks).
To get a pretty picture like the one above you have to do a few things. First, you have to enable AD Auditing and set some Advanced Auditing policies which will start logging some additional Event IDs to the Security Event log.
To get the LDAP information, we’ll need to start ingesting the Directory Service log. Active Directory records events to the Directory Services log. You can use the information collected to help you diagnose and resolve possible problems and monitor the activity of Active Directory-related events on your servers.
We’ll also need the SMB logs. This requires SMB Auditing to be turned on as well. Both WannaCry and Petya took advantage of environments that were still using SMBv1. When you have 1000s of servers, you might have one or two out there still running this old insecure protocol. This Workbook will help you find it.
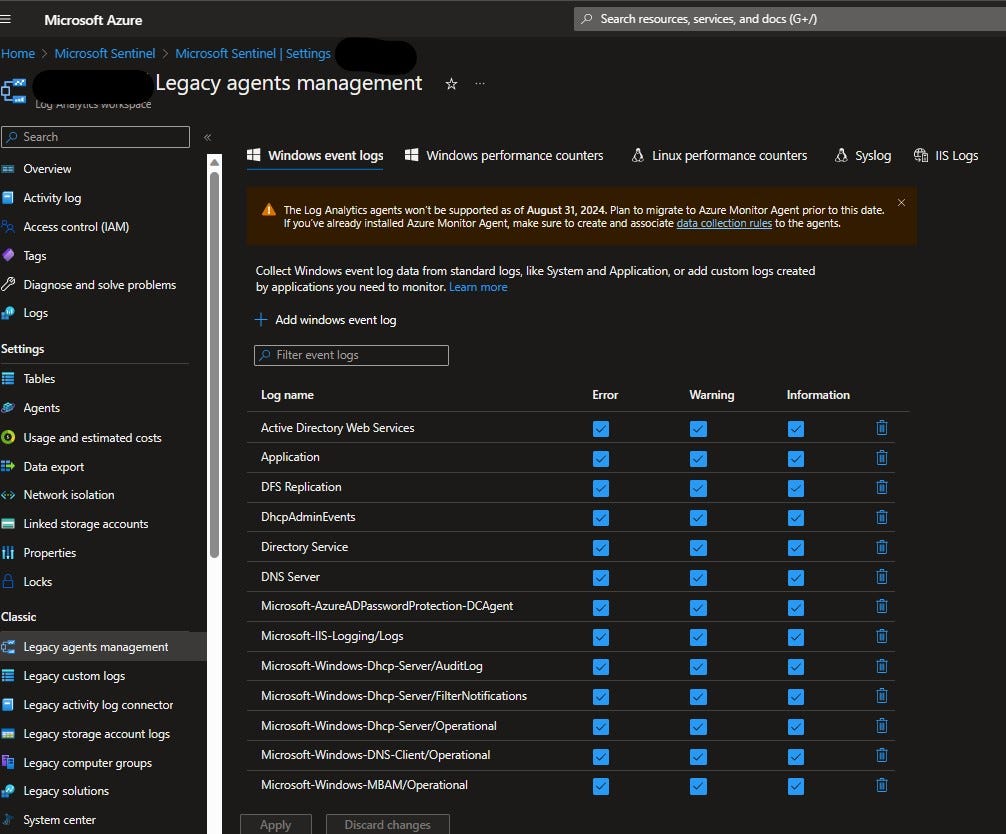
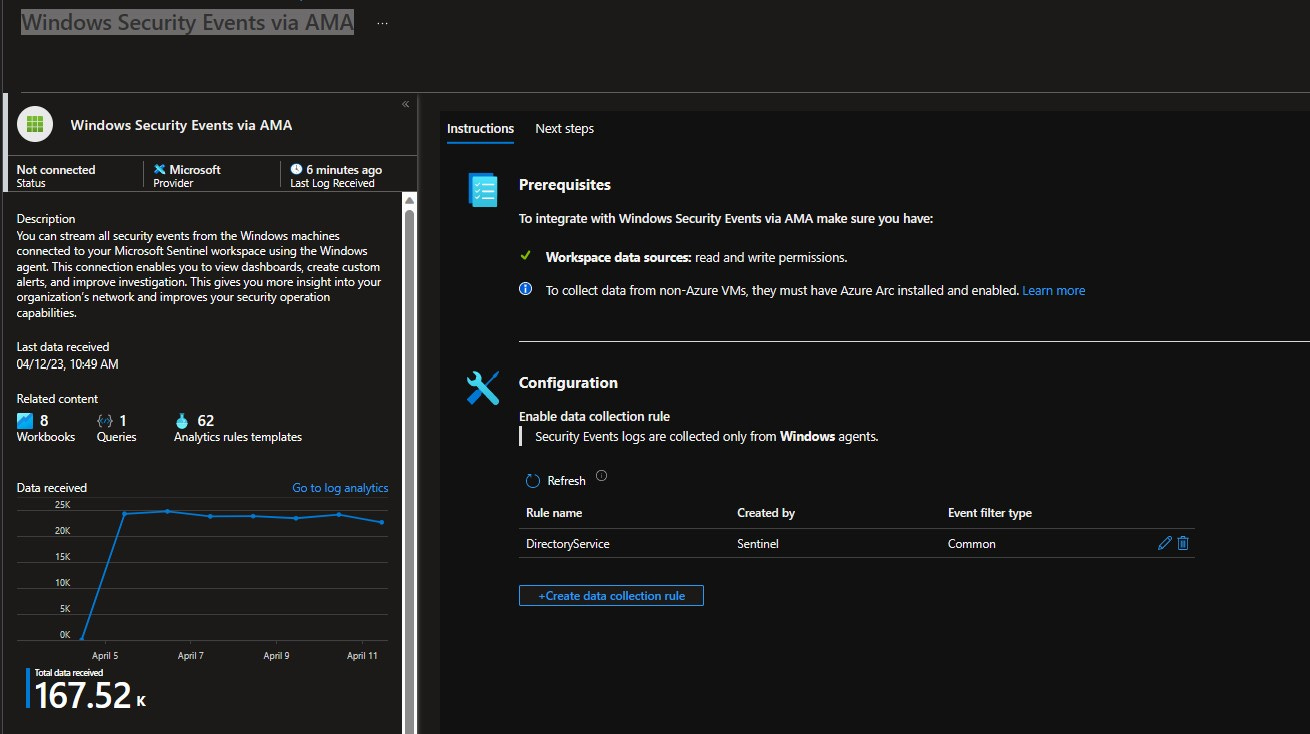
There are two ways to get this data flowing into Sentinel. It depends on whether you’re using the MMA agent (which goes out of support in August 2024) or the newer AMA.
For the MMA agent, you’ll open up Sentinel and click the “Settings” button on the bottom left. Then select “Legacy agents management”. From there, you click on the + sign next to “Add windows event log” and type in the name of the log you want.
If you’re using the AMA, click on “Data Connectors” inside the Sentinel portal. Then select “Windows Security Events via AMA” and create a new data collection rule. If you’re not sure how to do that, check out Rod Trent’s article here.
Thanks and happy logging!




Andrea, you are awesome!