What should I log in my SIEM?
Assessing the value of data
During the last year or so, I’ve done close to 70 Sentinel engagements with customers. We’ve set it up, turned on the data connectors and analytic rules then wait to see what kind of alerts and incidents come in. Working through incidents is always fun but one question that comes up over and over again during this process is “What data should I be bringing into my SIEM?”.
When a customer asks me that, I usually ask them a question. “How do you define the word SIEM”? At Microsoft we define it like this. “Security information and event management, SIEM for short, is a solution that helps organizations detect, analyze, and respond to security threats before they harm business operations.”
To me, that means that the information in your SIEM should contain properties that help you with real-time incident response and give you a centralized view of potential threats. You want to ingest data that gives you greater transparency when monitoring users, applications, and devices.
Over the years, on-premises SIEMs have become a dumping ground for logs. And it’s easy to understand why. You already have the massive amounts of storage you need to keep those logs and you need to retain them for X years because an auditor might need them or for a legal case. But do they really belong in your SIEM? Noise is the enemy of speed when it comes to investigating an incident so the less noise you have the faster you’ll be able to respond.
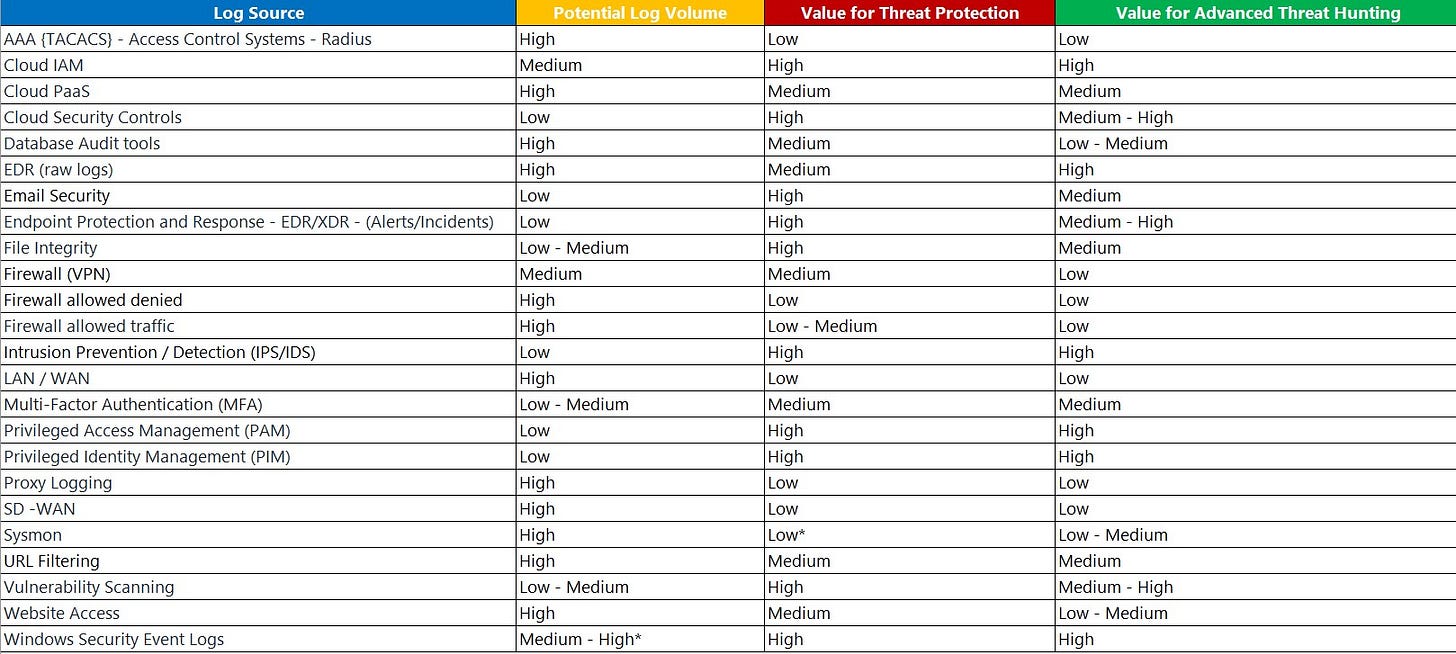
So, what logs should we bring into the SIEM? That can be different for each organization. But my dear friend and fellow Microsoft Security Insights show host created this table to illustrate the value of different types of logs. You can that ingesting denied firewall traffic has a high potential log volume but a low value for threat protection and threat hunting. Does that mean that you shouldn’t bring those logs into your SIEM? That’s for you to decide. But this list may help you ask questions about what logs have the most value for your enterprise.
The illustrious @rodtrent said recently “Anything with the word "flow" in it is usually of low value and costly.” Which is very funny but also 100% true when it comes to incident response.
.



Great post Andrea. Now I need to go link it to Sentinel tables & rules!
Thank you for writing this up, Andrea!